$35 Billion in Pens
What could the Texas Department of Health & Human Services possibly be doing with $35 billion in pens?
What could the Texas Department of Health & Human Services possibly do with $35 billion dollars worth of pens? Taking a break from the “Stolen Words” series, I’d like you to join me in a little thought exercise.
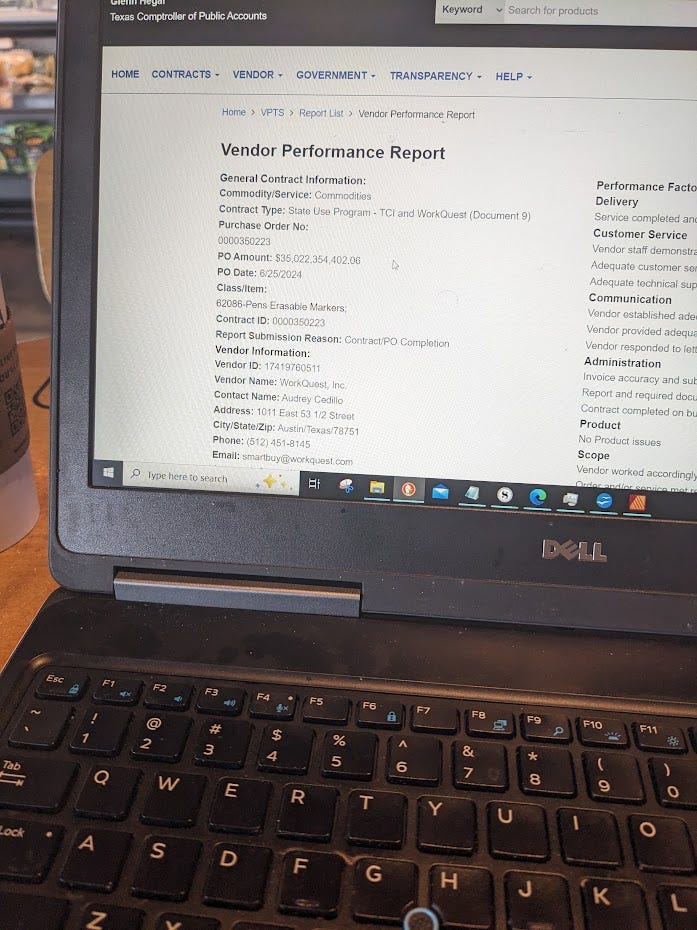
Photo taken on Friday, September 27th, of the vendor performance report on the Texas Smart Buy website for a purchase order issued by the Texas Department of Health & Human Services to Workquest on June 24, 2024 . The performance report was submitted on September 5, 2024. Link to a PDF of the performance report as it was when I discovered it.
This is a reposting of the article on my site, “$35 Billion in Pens.” Posting here because even though it is served through Cloudflare, the site is continually hit with DDoS attacks resulting in 503 errors.
Texas and Money
The Texas Department of Health & Human Services spent $35 billion to WorkQuest for “pens/erasable markers” this year. This was in addition to a purchase order for $32 billion for “printers and printer supplies” to the same company in October of 2023.
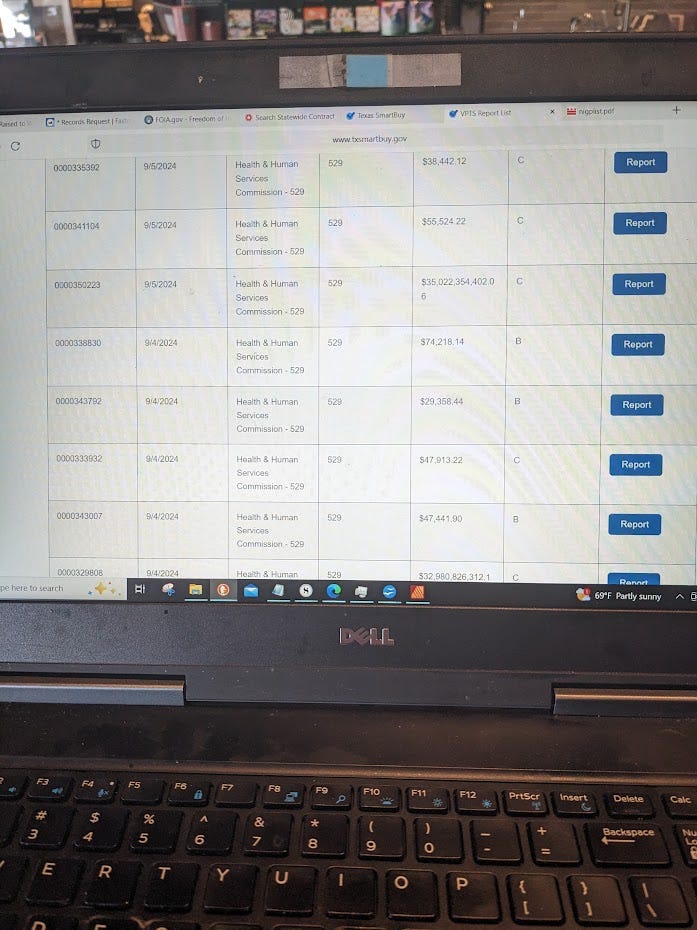
Photo taken Friday, September 27th, of the $35 billion contract amount in the long list of contracts with WorkQuest. It’s kind of hard to miss that one.
Late last year, I ID’d activities of sock puppet networks online. I realize that there are many marketing/social media agencies that just do business this way. Personally, I think that it is extremely deceptive. Beyond being misleading to clients, the stock puppets steal words, ideas, and stories from actual people and claim them as their own and the client’s account will end up getting burned for any natural and organic engagement.
However, the activities I saw these sock puppet networks engaged in went far beyond being unethical, there were many, many clearly illegal things going on.1 It was a criminal syndicate. I started calling the sock puppets out, I began getting hacked. (I also wrote a letter to the Humble ISD school board against chaplains in public schools and sent it to all 150 representatives in the Texas legislature at the end of December.)2
The hacking, attempts to locate me, and harassment on social media by floating targeted posts across my feed (see my first video in the hacked series for a description) continued, but I didn’t think I had anything concrete that I could go to authorities about.
In April, I had definite evidence of hacking of my laptop. I called the FBI, they told me to call the local police and file a report. I called the police, they told me it sounded like a virus (it very obviously wasn’t), dismissed it, and told me to call GeekSquad.
After I made the call to the FBI, the attacks intensified when the criminals realized authorities weren’t going to do anything.
A month later, in May, we discovered evidence of a bootleg listing of the Dostoevsky issue of An Unexpected Journal (I have since resigned from the board and withdrawn my association).3 The thieves were not using an Amazon ISBN that KDP provides for self-publishing. It seemed to me that it would be a simple thing to track down who the ISBN was issued to at Bowker and whose financial information was on the account at Amazon.
Again, I called the FBI. In addition to the cyberstalking, online harassment, and hacking, there was now a clear cut instance of intellectual property theft. The agent told me to file a report on IC3. I also went into the local police department and reported the IP theft and fraud to an officer. I wanted him to see what was happening in person. He advised me to get the listing removed to “stop the bleed” and then pursue whatever remedies were available afterward.
As someone had told me that the FBI won’t bother with hacking and online fraud that involve low dollar amounts, I spent the next two months documenting all of the fraudulent activities I had seen the sock puppet networks engage in as well as outlining different ways the mass of sock puppet accounts manipulating the algorithm could be used to target, defraud and exploit people. I knew that attacking me was not the only thing the people behind the hacking were doing.
The report ended up being 30,000 words and 198 pages including 100 pages of exhibits with screenshots illustrating what I was seeing. I submitted it to tips.fbi.gov and Ic3.org. I also submitted a complaint to the Department of Justice as I was certain that the continual dismissal of my complaint in spite of flagrant and obvious offenses was because I am a woman with a Hispanic last name.
I submitted the report on July 28, 2024.
As of today [September 28th], I have yet to receive a single response or even acknowledgement from the FBI. The only response I received was a form letter from the Department of Justice saying they were dismissing the complaint without any investigation. The same thing happened after the July submission that happened in April, once the criminals knew that authorities weren’t going to do anything, the attacks got exponentially worse.
The next day, July 29th, began the next level of discovery.
Systematized Intellectual Property Theft
I came across a major Christian platform that had multiple devotional series that looked like they were spun versions of the devotional I published in 2019, #NoFear. They had reflections that used the exact words of my prayer in my live Bible studies.
Recognizing sock puppet activity in a Facebook group for Christian book reviews, I came across a site they were promoting that looked like they were attempting to clone An Unexpected Journal and as well as take over the name recognition of a long-running site of someone I knew that had let the site go because it had continually been hacked in the last year they were running it (sabotage is a continual theme in all of this). On this doppleganger site, I recognized the plagiarized work of people I knew.
This was just the beginning. I continued to find site after site and social media profile after social media profile using plagiarized words of either myself or people I knew. I edited for six years for An Unexpected Journal and I’ve edited a lot of writers. Our work had been stolen by either lazy ghostwriters or used to train an AI model, likely both.
This first week in August was also when I began to realize that the people behind the theft and attacks weren’t just nameless people on the internet, but people I knew.
Discovery Timeline
On August 4th, I did a three hour livestream explaining what was going on and how the sock puppet networks were operating.4
On August 5th, my Facebook login was suspended. When I was finally able to log back in, I could tell they had hacked my accounts. I also reformatted my phone. This was a big mistake as I am fairly certain that reinstallation was a corrupted operating system. All of the main Google apps were weird. This is a Google Pixel phone on the T-Mobile network. They were hacking through Google log-ins.5 Any time I would log in, it would prompt two one-time passwords so the hacker could log in as well.
On August 7th, I went back into the local police department as my phone was completely compromised. I wanted to make a report. I spoke to the same officer that I spoke to in May. His demeanor was completely different, condescending and dismissive. He told me hacking wasn’t a crime; that what I experienced wasn’t reality; and that I needed mental help. He was on crutches.6
In the report submitted to the FBI, I said he was the only person who had been helpful so far. I think the people targeting me read the report and threatened him. I think that either the FBI submission sites are either completely insecure or there are people on the take in the FBI that gave them the information. That is the only explanation for a police officer to say such a blazingly flagrant lie that hacking isn’t a crime.
The month of August was spent securing my accounts and trying to get my laptop to function. I reformatted the laptop, wiping all the data. If it was a software issue, this should have taken care of the problem. It did not. Even without accessing the internet, they were able to hack and crash my laptop, which is why I think they are using my laptop identifier to hack.
It was one thing after another. There are updates in the Hacked saga as I came across new information.7
I could tell that whoever was running the the sock puppet accounts promoting the Texas Parks Department was involved in siphoning off what I published (one of them used an experience I shared on Facebook at a Texas park in their updates). I knew some of the people involved and I was fairly certain they were running a content/PR agency using stolen content and faked engagement, but I didn’t know the agency name they were operating under.
As some of their clients are public agencies, I knew I could submit a FOIA request for that information. But if you’ve ever actually submitted a FOIA request, especially in Texas, they seem to do everything they can to delay or avoid fulfilling your request entirely.
If a vendor had won a contract for social media/PR services, that information should be publicly available on the Texas Smart Buy site.8 I searched for contracts using every single NIGP code that was related to communication, advertising, and digital media.9 No contracts came up. (I also discovered that even in the use of these codes, someone in Texas is making money.)10
Then I just started scrolling through the contracts awarded to different vendors that the Texas Parks Department worked with, one of which is WorkQuest.11 Workquest also provides services for a number of Texas agencies.
That is when I stumbled across the performance report for a P.O. for $35 billion in pens issued by the Texas Department of Health and Human Services to WorkQuest on June 25, 2024. There was no way to miss it. I found a second performance report for another P.O. issued on October 4, 2023. Both of the performance reports were submitted on September 5, 2024.
I did a livestream about this on Saturday, September 28th.12 By Tuesday, October 1st, those purchase orders had been edited to more reasonable amounts.
https://youtube.com/live/36i3WXnJmgQ
How Does This Happen?
But the question still remains … how in the hell does not one, but two, purchase orders/vendor performance reports for such outrageous amounts get overlooked?
Isn’t there some sort of reconciliation that happens? Does no one review this? Because even without any auditing or oversight on the part of the State of Texas, someone at WorkQuest should have noticed the error … if it was an error.
The amounts of the P.O.’s in the performance reports have since been edited, but the fact that the digital record was edited does not change the fact that the report was to give an account of actual money that was spent. The digital record is supposed to be a reflection of reality. The original number was either wrong when it was submitted or the edited numbers are wrong now.
In my mind, two purchase orders totaling $67 billion raise questions about financial oversight and auditing in the State of Texas. I wasn’t looking for those particular purchase orders, they just stood out because all those numbers were wrapping in the column for contact amount.
Money is math. How did a reconciliation not catch those grossly out-of-balance amounts? What is the review process, both on the part of the State of Texas and WorkQuest, that no one noticed performance reports for such crazy amounts?
As a friend pointed out, $32 billion, the amount of the purchase order issued on October 4, 2023, is the amount of the Texas budget surplus in the last legislative session that Greg Abbott is withholding from Texas schools.
My Thoughts
These are my thoughts about those two purchase orders. Texas has a $32 billion surplus13 from the last Texas biennial budget that Greg Abbott has been withholding from Texas schools in a bid to shove vouchers down the throat of Texas legislators.14
This is what I know. I know that Greg Abbott is sold out to ogliarchs.
I know that Abbott is hell-bent on destroying public education.
I know that the people behind the sock puppet network that stole my intellectual property and have been hacking and harassing me also use that sock puppet network to promote accounts affiliated with the State of Texas.
I know that the people behind the network use AI to develop personas and generate the comments used by the mass of sock puppet accounts.
I know that they use AI models built by stolen intellectual property for ghostwriting and their own publications, written, audio and video.
I also know that the majority of the people that I know that are involved in the content and fake engagement ring are homeschoolers … and no, I don’t think they care about public school children in Texas. They literally think that teaching or attending a public school is a fate worse than death.
Based on all of this, I think those funds are going to build an AI model that will replace public education in Texas, except for the worthy few that will get vouchers to subsidize their private, real education.
That is my guess.
Of course, it could be that Glenn Hagar and the entire comptroller department are just completely and utterly incompetent and there are no checks in place at all.
We’ll see. You can’t hide the movement of $67 billion.
What AI Can’t Do
After the events of the past year, I feel very strongly that AI, and specifically ChatGPT, are nothing more than systematized intellectual property theft.
AI does not “generate” it’s own thoughts and words. It is an algorithm. No matter what kind of name and face you put to it, it is still just an algorithm.
AI quantifies. It cannot qualify.
AI cannot assess value. It cannot tell whether something is “good” or not. All it can do is count the number of times a particular position or statement has been made, and that a particular statement has been repeated most does not make it true. The mass can be wrong.
AI assembles words and thoughts from multiple people that have written on a topic and assembles them. The problem is that those pieces can be taken from arguments that are building to very different conclusions.
This is especially evident in AI generated answers (which search engines are using to steal traffic from the authors and web publishers providing those answers) on anything related to theology or the Bible. They are absolutely horrendous. If you don’t know, you might buy the answer, but that is the point. You are only search if you don’t know, and so AI is feeding ignorance.
AI is designed to be self-referential. It “learns” from positive reinforcement. What the learner/reader/searcher responds positively to is what they will receive more of.
This is antithetical to true education.
Education, true learning, is not there to serve you. Truth is truth. In order to learn, to enlighten our ignorance, we have to be willing to recognize where we are in error. Often, we cannot see that error unless it is pointed out by someone who has mastery in the area we wish to learn.15
Trying to supplant human beings with an AI model is taking constructivism to the extreme. As I wrote six years ago for An Unexpected Journal on constructivism in education,
It is not only “individualized learning,” but “individualized truth.” A student conditioned in constructivism can easily believe that their position is the correct one regardless of all evidence to the contrary because in the constructivist approach, all information is interpreted through their own perceptions and existing knowledge. If one of the common goals of an educational system is to create “global citizens”[13] and “good communicators,” a constructivist mindset undermines that goal. A community is that in which individuals come together for a common goal and purpose. Communication is achieved through the transmission of ideas and concepts through agreed upon language. If we cannot begin on common ground and discuss differences of opinion with an assumption that there actually is a point of agreement that can be reached, we condemn ourselves to living on isolated islands either in contention or domination of another. As Lewis notes, “For the power of Man to make himself what he pleases means, as we have seen, the power of some men to make other men what they please.”[14] Citizenship is about community. When we talk about citizenship, it should mean there is a coming together in agreement on certain truths.
WorkQuest Performance Reports as of September 27th
Further Reading
If you are hacked, the instructions you will find on all relevant government sites is that you are to report it to the FBI. From my personal experience, it is worthless to report it. The only thing that happened after I have contacted the FBI multiple times is that the perpetrators were emboldened to go to greater extremes.
Reporting Computer, Internet-related, Or Intellectual Property Crime
https://www.justice.gov/criminal/criminal-ccips/reporting-computer-internet-related-or-intellectual-property-crime
Internet Crime Complaint Center (IC3)
https://www.ic3.gov/
What We Investigate:
https://www.fbi.gov/investigate/cyber
The Cyber Threat
Malicious cyber activity threatens the public’s safety and our national and economic security. The FBI’s cyber strategy is to impose risk and consequences on cyber adversaries. Our goal is to change the behavior of criminals and nation-states who believe they can compromise U.S. networks, steal financial and intellectual property, and put critical infrastructure at risk without facing risk themselves. To do this, we use our unique mix of authorities, capabilities, and partnerships to impose consequences against our cyber adversaries.The FBI is the lead federal agency for investigating cyber attacks and intrusions. We collect and share intelligence and engage with victims while working to unmask those committing malicious cyber activities, wherever they are.
Learn more about what you can do to protect yourself from cyber criminals, how you can report cyber crime, and the Bureau’s efforts in combating the evolving cyber threat.
If you’ve been hacked, don’t count on the police for help
Even the FBI and your local police can’t agree on who you should contact first.
https://www.cnet.com/news/privacy/when-you-get-hacked-figuring-out-who-to-call-for-help-can-be-a-puzzle/
An email pops up in your inbox and your eyes widen. A stranger claims to have video footage of you watching porn and asks for $1,000.
There’s outrage and embarrassment. You reach for your phone. But then you wonder, “Who do I even call?”
Unfortunately, the answer to that question is complicated.
As it turns out, even law enforcement officials can’t agree. The FBI and your local police both suggest that you should call them. But experts warn that in many cases, neither agency will be able to help, especially if the criminal is asking for so little money.
This dynamic underscores why these kinds of hacks — and yes, the porn scam really happened — are starting to proliferate. There’s no clear answer on who to call. And from law enforcement’s perspective, many of these crimes are too small to be worth prosecuting. It’s no surprise that cyberattacks have run rampant across the web, as thieves online find ways to steal credit card information from millions of people without leaving their homes.
“If the people doing it keep the dollar amounts small enough that no individual police department is going to be motivated enough to prosecute, you can collect a lot of money from a lot of people all around the world,” said Adam Bookbinder, the former chief of the US Attorney’s cybercrime unit in the district of Massachusetts.
When You Get Hacked, Figuring Out Who to Call for Help Can Be a Puzzle https://www.cnet.com/news/privacy/when-you-get-hacked-figuring-out-who-to-call-for-help-can-be-a-puzzle/
August 1, 2007: NASA Spent Millions on a Pen Able to Write in Space
https://www.scientificamerican.com/article/nasa-spent-millions-on-a-pen-able-t/
https://x.com/RaisedtoWalk/status/1788901523118006324
Carla M. Sallee Alvarez, "A Message to My Stalker," Raised to Walk, August 4, 2024, accessed October 28, 2024, https://raisedtowalk.org/hacked/a-message-to-my-stalker/
Carla M. Sallee Alvarez, "Against Chaplains in Public Schools," Raised to Walk, December 21, 2023, accessed October 28, 2024, https://raisedtowalk.org/the-walk/against-chaplains-in-public-schools/
Carla M. Sallee Alvarez, "Why I'm No Longer Associated with An Unexpected Journal," Raised to Walk, August 18, 2024, accessed October 28, 2024, https://raisedtowalk.org/hacked/why-im-no-longer-associated-with-an-unexpected-journal/
Alvarez, “A Message to My Stalker.”
Carla M. Sallee Alvarez, "Hacked through Google," Raised to Walk, August 13, 2024, accessed October 28, 2024, https://raisedtowalk.org/hacked/hacked-through-google/
Carla M. Sallee Alvarez, "The Woodburn Police Said Hacking Isn't a Crime," Raised to Walk, August 13, 2024, accessed October 28, 2024, https://raisedtowalk.org/hacked/the-woodburn-police-said-hacking-isnt-a-crime/
Carla M. Sallee Alvarez, "Hacked: the Saga," Raised to Walk, accessed October 28, 2024, https://raisedtowalk.org/hacked-the-saga/
Texas Smart Buy, Glenn Hagar: Texas Comptroller of Public Accounts, accessed October 28, 2024, https://www.txsmartbuy.gov/
"NIGP Code," Wikipedia, accessed October 28, 2024, https://en.wikipedia.org/wiki/NIGP_Code
"Organize and Optimize Procurement," Periscope by SOVRA, accessed October 28, 2024, https://www.periscopeholdings.com/buyer-solutions/nigp#
"Browse Contracts," Texas Smart Buy, Glenn Hagar: Texas Comptroller of Public Accounts, accessed October 28, 2024, https://www.txsmartbuy.gov/browsecontracts
Carla M. Sallee Alvarez, "$35 Billion in Pens!", Raised to Walk, September 28, 2024, accessed October 28, 2024, https://raisedtowalk.org/hacked/35-billion-on-pens/
Karen Brooks Harper, Yuriko Schumacher, and Alex Ford, "How Could Texas spend its record $32.7 billion surplus?" Texas Tribune, March 13, 2023, accessed October 28, 2024. https://www.texastribune.org/2023/03/13/texas-budget-surplus/
Jeremy Schwartz, "Texas Is the Largest GOP Stronghold Without Pro-School Voucher Legislation. Gov. Abbott Is on a Crusade to Change That." Propublica, June 21, 2024, accessed October 28, 2024, https://www.propublica.org/article/texas-greg-abbott-crusade-for-school-vouchers
Steven Dial, "Gov. Abbott 'certain' school vouchers will pass next session," Fox 4 KDFW, April 21, 2024, https://www.fox4news.com/news/texas-school-vouchers-greg-abbott-interview
Patrick Svitek, Zach Despart, and Brian Lopez, "How Gov. Greg Abbott lost a yearlong fight to create school vouchers," Texas Tribune, December 22, 2023, accessed October 28, 2024. https://www.texastribune.org/2023/12/22/texas-school-vouchers-greg-abbott/
Blaised Gainey, "Texas lawmakers kick off a new season of heated debate over school vouchers," Texas Public Radio, August 13, 2024, accessed October 28, 2024. https://www.tpr.org/news/2024-08-13/texas-lawmakers-kick-off-a-new-season-of-heated-debate-over-school-vouchers
"Will Texas have a budget surplus next year?" Texas 2036, accessed October 28, 2024. https://texas2036.org/posts/will-texas-have-a-budget-surplus-next-year/
Cecile Young and Trey Wood, "Legislative Appropriations Request for Fiscal Years 2026-2027," Texas Health and Human Services, September 30, 2024, accessed October 28, 2024, https://www.hhs.texas.gov/sites/default/files/documents/lar-joint-budget-hearing-fy2026-2027.pdf
Carla M. Sallee Alvarez, “From the Green Book to The River: Lewis, Relativism, and Constructivism in Education.” An Unexpected Journal 1, no. 1 (Spring 2018): 121-41. accessed October 28, 2024. https://anunexpectedjournal.com/from-the-green-book-to-the-river-lewis-relativism-and-constructivism-in-education/
“… as Barbara Jaworski notes in a review of Constructivism in Education, education does not involve students alone but rather it is “fundamentally about students and teachers and the process of teaching.”[7] Pedagogy is a two-way process. Information is transmitted to the student, and the teacher must be able to discern if that information has been received and understood. In his discussion The Meanings of Truth, Thomas Aquinas reasoned that for a thing to be investigated, there must be absolute truth apart from and outside of the individual and the state of being, otherwise “all science and knowledge of things would perish.”[8] Regardless of educational ideology, an effective teacher is one which can both engage the students’ interest and modify their teaching to the students’ unique needs and learning styles. While both are “student centered,” practical constructivism ranges from focusing on the characteristics of all forms of effective teaching which incorporates feedback from the learner and what Aquinas would call the “diverse ways”[9] in which a particular truth can be understood to radical constructivism which operates on the basis that all knowledge is subjective and reality is “objectively unknowable.”[10]